Author Archive
April 13, 2022
Game Governance Domains: a NFT Support Nightmare
“I was working on an online trading-card game in the early days that had player-to-player card trades enabled through our servers. The vast majority of our customer support emails dealt with requests to reverse a trade because of some kind of trade scams. When I saw Hearthstone’s dust system, I realized it was genius; they probably cut their support costs by around 90% with that move alone.”
Ian Schreiber
A Game’s Governance Domain
There have always been key governance requirements for object trading economies in online games, even before user-generated-content enters the picture. I call this the game’s object governance domain.
Typically, an online game object governance domain has the following features (amongst others omitted for brevity):
- There is usually at least one fungible token currency
- There is often a mechanism for player-to-player direct exchange
- There is often one or more automattic markets to exchange between tokens and objects
- May be player to player transactions
- May be operator to player transactions (aka vending and recycling machinery)
- Managed by the game operator
- There is a mechanism for reporting problems/disputes
- There is a mechanism for adjudicating conflicts
- There are mechanisms for resolving a disputes, including:
- Reversing transactions
- Destroying objects
- Minting and distributing objects
- Minting and distributing tokens
- Account, Character, and Legal sanctions
- Rarely: Changes to TOS and Community Guidelines
In short, the economy is entirely in the ultimate control of the game operator. In effect, anything can be “undone” and injured parties can be “made whole” through an entire range of solutions.
Scary Future: Crypto? Where’s Undo?
Introducing blockchain tokens (BTC, for example) means that certain transactions become “irreversible”, since all transactions on the chain are 1) Atomic and 2) Expensive. In contrast, many thousands of credit-card transactions are reversed every minute of every day (accidental double charges, stolen cards, etc.) Having a market to sell an in-game object for BTC will require extending the governance domain to cover very specific rules about what happens when the purchaser has a conflict with a transaction. Are you really going to tell customers “All BTC transactions are final. No refunds. Even if your kid spent the money without permission. Even if someone stole your wallet”?
Nightmare Future: Game UGC & NFTs? Ack!
At least with your own game governance domain, you had complete control over IP presented in your game and some control, or at least influence, over the games economy. But it gets pretty intense to think about objects/resources created by non-employees being purchased/traded on markets outside of your game governance domain.
When your game allows content that was not created within that game’s governance domain, all bets are off when it comes to trying to service customer support calls. And there will be several orders of magnitude more complaints. Look at Twitter, Facebook, and Youtube and all of the mechanisms they need to support IP-related complaints, abuse complaints, and robot-spam content. Huge teams of folks spending millions of dollars in support of Machine Learning are not able to stem the tide. Those companies’ revenue depends primarily on UGC, so that’s what they have to deal with.
NFTs are no help. They don’t come with any governance support whatsoever. They are an unreliable resource pointer. There is no way to make any testable claims about any single attribute of the resource. When they point to media resources (video, jpg, etc.) there is no way to verify that the resource reference is valid or legal in any governance domain. Might as well be whatever someone randomly uploaded to a photo service – oh wait, it is.
NFTs have been stolen, confused, hijacked, phished, rug-pulled, wash-traded, etc. NFT Images (like all internet images) have been copied, flipped, stolen, misappropriated, and explicitly transformed. There is no undo, and there is no governance domain. OpenSea, because they run a market, gets constant complaints when there is a problem, but they can’t reverse anything. So they madly try to “prevent bad listings” and “punish bad accounts” – all closing the barn door after the horse has left. Oh, and now they are blocking IDs/IPs from sanctioned countries.
So, even if a game tries to accept NFT resources into their game – they end up in the same situation as OpenSea – inheriting all the problems of irreversibility, IP abuse, plus new kinds of harassment with no real way to resolve complaints.
Until blockchain tokens have RL-bank-style undo, and decentralized trading systems provide mechanisms for a reasonable standard of governance, online games should probably just stick with what they know: “If we made it, we’ll deal with any governance problems ourselves.”
August 5, 2021
February 7, 2017
Open Source Lucasfilm’s Habitat Restoration Underway
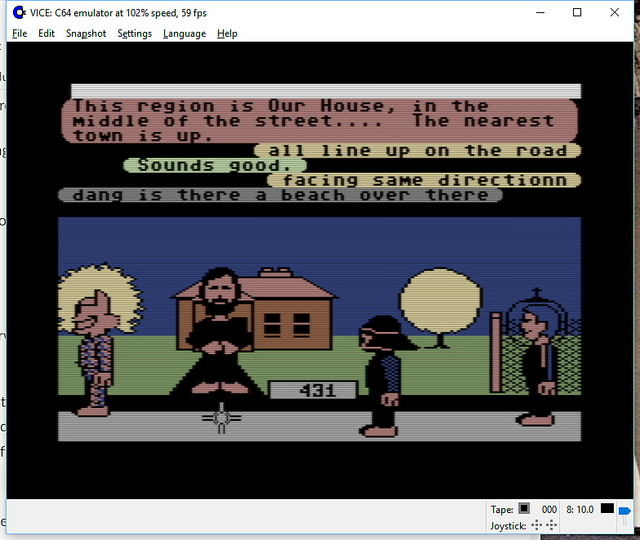
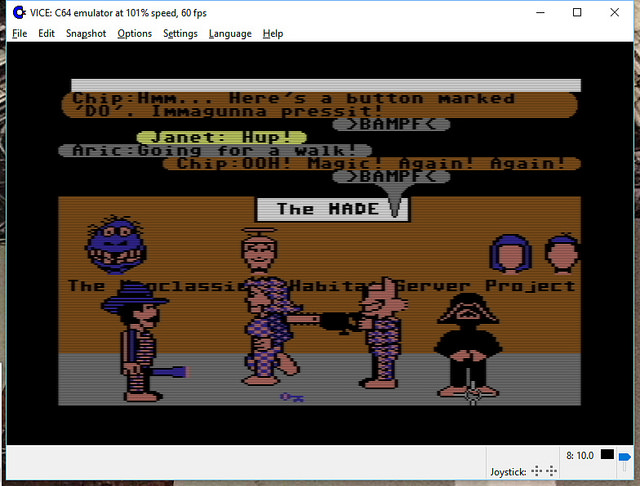
It’s all open source!
Yes – if you haven’t heard, we’ve got the core of the first graphical MMO/VW up and running and the project needs help with code, tools, doc, and world restoration.
I’m leading the effort, with Chip leading the underlying modern server: the Elko project – the Nth generation gaming server, still implementing the basic object model from the original game.
http://neohabitat.org is the root of it all.
http://slack.neohabitat.org to join the project team Slack.
http://github.com/frandallfarmer/neohabitat to fork the repo.
To contribute, you should be capable to use a shell, fork a repo, build it, and run it. Current developers use: shell, Eclipse, Vagrant, or Docker.
To get access to the demo server (not at all bullet proofed) join the project.
We’ve had people from around the world in there already! (See the photos)
http://neohabitat.org #opensource #c64 #themade
April 29, 2014
Troll Indulgences: Virtual Goods Patent Gutted [7,076,445]
 Another terrible virtual currency/goods patent has been rightfully destroyed – this time in an unusual (but worthy) way: From Law360: EA, Zynga Beat Gametek Video Game Purchases Patent Suit, By Michael Lipkin
Another terrible virtual currency/goods patent has been rightfully destroyed – this time in an unusual (but worthy) way: From Law360: EA, Zynga Beat Gametek Video Game Purchases Patent Suit, By Michael Lipkin
Law360, Los Angeles (April 25, 2014, 7:20 PM ET) — A California federal judge on Friday sided with Electronic Arts Inc., Zynga Inc. and two other video game companies, agreeing to toss a series of Gametek LLC suits accusing them of infringing its patent on in-game purchases because the patent covers an abstract idea. … “Despite the presumption that every issued patent is valid, this appears to be the rare case in which the defendants have met their burden at the pleadings stage to show by clear and convincing evidence that the ’445 patent claims an unpatentable abstract idea,” the opinion said.
The very first thing I thought when I saw this patent was: “Indulgences! They’re suing for Indulgences? The prior art goes back centuries!” It wasn’t much of a stretch, given the text of the patent contains this little fragment (which refers to the image at the head of this post):
Alternatively, in an illustrative non-computing application of the present invention, organizations or institutions may elect to offer and monetize non-computing environment features and/or elements (e.g. pay for the right to drive above the speed limit) by charging participating users fees for these environment features and/or elements.
WTF? Looks like reasoning something along those lines was used to nuke this stinker out of existence. It is quite unusual for a patent to be tossed out in court. Usually the invalidation process has to take a separate track, as it has with other cases I’ve helped with, such as The Word Balloon Patent. I’m very glad to see this happen – not just for the defendant, but for the industry as a whole. Just adding “on a computer [network]” to existing abstract processes doesn’t make them intellectual property! Hopefully this precedent will help kill other bad cases in the pipeline already…
March 5, 2014
Two Recipes for Stone Soup [A Fable of Pre-Funding Startups]
There once was a young Zen master, who had earned a decent name for himself throughout the land. He was not famous, but many of his peers knew of his reputation for being wise and fair. During his career, he was renowned for his loyalty to whatever dojo he was attached to, usually for many years at a time. One year his patronage decided to merge with another, larger dojo, and the young master found himself unexpectedly looking for a new livelihood. But he was not desperate, as he’d heeded the words of his mentor and had kept close contact with many other Zen masters over the years and considered many options.
As word spread about the young master’s availability, he began to receive more interest than he could possibly ever fulfill. It took all of his Zen training and long nights just to keep up with the correspondence and meetings. He was getting queries from well-established cooperatives, various governments, charitable groups, many recently formed houses, and even more people who had a grand idea around which to form a whole-new kind of dojo. This latter category was intriguing, but the most fraught with peril. There were too many people with too many ideas for the young master to sort between. So he decided to consult with his mentor. At least one more time, he would be the apprentice and ventured forth to the dojo of his youth, a half-day’s journey away.
“Master, the road ahead is filled with many choices, some are well traveled roads and others are merely slight indentations in the grass that may some day become paths. How can I choose?” asked the apprentice.
The mentor replied, “Have you considered the wide roads and the state-maintained roads?”
“Yes, I know them well and have many reasons to continue on one of them, but these untrodden paths still call to me. It is as if there is a man with his hands at his mouth standing at each one shouting to follow his new path to riches and glory. How do I sort out the truth of their words?” The young master was genuinely perplexed.
“You are wise, my son, to seek council on this matter — as sweet smelling words are enticing indeed and could lead you down a path of ruin or great fortune. Recount to me now two of the recruiting stories that you have heard and I will advise you.” The mentor’s face relaxed and his eyes closed as he dropped into thought, which was exactly what the young master needed to calm himself sufficiently to relate the stories.
After the mentor had heard the stories, he continued meditating for several minutes before speaking again: “Former apprentice, do you recall the story and lesson of Stone Soup?”
“Yes, master. We learned it as young adepts. It is the story of a man who pretended that he had a magic stone for making the world’s best soup, which he then used to convince others to contribute ingredients to the broth until a delicious brew was made. This story was about how leadership and an idea can ease people into cooperating to create great things for the good of them all.” recounted the student. “I can see the similarity between the callers standing on the new paths and the man with the magic stone. Also it is clear that that the ingredients are symbolic of the skills of the potential recruits. But, I don’t see how that helps me.” The apprentice had many years of experience with the mentor, and knew that this challenge would get the answer he was looking for.
“The stories you told me are two different recipes for Stone Soup,” the master started.
“The first caller was a man with a certain and impressive voice that said to you ‘You should join my dojo! It is like none other and it is a good and easy path that will lead to great riches. Many people that you know, such as Haruko and Jin, have tested this path and others who have great reputations including Master Po and Teacher Win are going to walk upon it as well. Your reputation would be invaluable to our venture. Join us now!'”
“The second caller was a humble and uncertain man who spoke softly as he said ‘You should join my dojo. It is like none other and the path, though potentially fraught with peril, could lead to riches if the right combination of people were to take to it. Your reputation is well known, and if you were to join the party, the chance of success would increase greatly. Would you consider meeting here in two days time to talk to others to discuss our goals and to see if a suitable party could be formed? Even if you don’t join us, any advice you have would be invaluable.” The mentor paused to see if his former student understood.
The young master said “I don’t see much difference, other than the second man seems the weaker.”
The mentor suppressed a sigh. Clearly this visit would not have been necessary if the young master were able to see this himself. Besides, it was good to see his student again and to be discussing such a wealth of opportunities.
He resumed, “Remember the parable of Stone Soup. The first man did not. He recited many names as if those names carried the weight of the reputations of their owners. He has forgotten the objective of the parable: The Soup. It is not the names or reputations of the people who placed the ingredients into the soup that mattered. It was that the soup needed the ingredients and the people added them anonymously, in exchange for a bowl of the broth. The first man merely suggested that important people were committed to the journey. I am quite certain that, were you to ask Haruko and Jin what names they have heard as being associated with the proposed dojo, you would find that your name was provided as a reference without your knowledge or consent.”
The student clearly became agitated as the truth of his mentor’s words sunk in. There was work to do before the day was done in order to repair any damage to his reputation that speaking with the first man may have caused.
The mentor continued, “The first recipe for Stone Soup is The Braggarts Brew. It tastes just like hot water because when everyone finds out that the founder is a liar, they all recover whatever ingredients they can to take them home and try to dry them out.”
The mentor took a quick drink, but gave a quelling glance that told the apprentice to remain silent until the lesson was over.
“You called the second man weaker, but his weakness is like that of the man with the Stone from the parable. He keeps his eyes on the goal — creating the Soup or staffing his dojo. Without excellent ingredients, there will be no success; and the best way to get them is to appeal to the better nature of those who possess them. He, by listening to them, transforms the dojo into a community project — which many contribute to, even if only a little bit.”
“Your skills, young master, are impressive on their own. You need not compare yourself with others, nor should you be impressed with one who would so trivially invoke the reputation of others, as if they were magic words in some charm.”
“The second recipe for Stone Soup is Humble Chowder, seasoned with a healthy dash of realism. This is the tempting broth.” And the mentor was finished.
The apprentice jumped up — “Master! I am so thankful! I knew that coming to you would help me see the truth. And now, I see a greater truth — you are also the man with a Stone. Please tell me what I can contribute to your Soup.”
“Choose your next course wisely, and return to me with the story so that I may share it with the next class of students.”
“I will!”
And with that, the young master ran as quickly as he could to catch up with the group meeting about the second man’s dojo. He wasn’t certain if he’d join them, but the honor of being able to contribute to its foundation would enough payment for now. When he approached the seated group, he was delighted to see several people whose reputation he respected around the fire, discussing amazing possibilities. One of them was Jin, who was shocked to learn that the first man had given his name to the young master…
[This is a long-lost post, originally posted on our old site six years go. Once again, the internet archive to the rescue!]
February 21, 2014
White Paper: 5 Questions for Selecting an Online Community Platform
Today, we’re proud to announce a project that’s been in the works for a while: A collaboration with Community Pioneer F. Randall Farmer to produce this exclusive white paper – “Five Questions for Selecting an Online Community Platform.”Randy is co-host of the Social Media Clarity podcast, a prolific social media innovator, and literally co-wrote the book on Building Web Reputation Systems. We were very excited to bring him on board for this much needed project. While there are numerous books, blogs, and white papers out there to help Community Managers grow and manage their communities, there’s no true guide to how to pick the right kind of platform for your community.
In this white paper, Randy has developed five key questions that can help determine what platform suits your community best. This platform agnostic guide covers top level content permissions, contributor identity, community size, costs, and infrastructure. It truly is the first guide of its kind and we’re delighted to share it with you.
Go to the Cultivating Community post to get the paper.
December 19, 2013
Audio version of classic “BlockChat” post is up!
On the Social Media Clarity Podcast, we’re trying a new rotational format for episodes: “Stories from the Vault” – and the inaugural tale is a reading of the May 2007 post The Untold History of Toontown’s SpeedChat (or BlockChattm from Disney finally arrives)

Link to podcast episode page[sc_embed_player fileurl=”http://traffic.libsyn.com/socialmediaclarity/138068-disney-s-hercworld-toontown-and-blockchat-tm-s01e08.mp3″]
October 30, 2013
Origin of Avatars, MMOs, and Freemium
Origin of Avatars, MMOs, and Freemium – S01E06 Social Media Clarity Podcast
The latest episode of the Social Media Clarity Podcast contains an interview with Chip Morningstar (and podcast hosts: Randy Farmer and Scott Moore). This segment focuses on the emergent social phenomenon encountered the first time people used avatars with virtual currency, and artificial scarcity.
Links and transcription at http://socialmediaclarity.net
August 26, 2013
Randy’s Got a Podcast: Social Media Clarity
I’ve teamed up with Bryce Glass and Marc Smith to create a podcast – here’s the link and the blurb:
Social Media Clarity – 15 minutes of concentrated analysis and advice about social media in platform and product design.
First episode contents:
News: Rumor – Facebook is about to limit 3rd party app access to user data!
Topic: What is a social network, why should a product designer care, and where do you get one?
Tip: NodeXL – Instant Social Network Analysis
August 23, 2013
Patents and Software and Trials, Oh My! An Inventor’s View
What does almost 20 years of software patents yield? You’d be surprised!
I gave an Ignite talk (5 minutes: 20 slides advancing every 15 seconds) entitled
“Patents and Software and Trials, Oh My! An Inventor’s View”
Here’s some improved links…
-
I’ve created ip-reform.org to support the “I Won’t Sign Bogus Patents” pledge.
-
Encourage your company to adopt Twitter’s Inventor’s Patent Agreement
-
Support the The EFF on Patent Reform – DefendInnovation.org has a proposal
-
Sequestration has delayed a bay area PTO office, support this bill
I gave the talk twice, and the second version is also available (shows me giving the talk and static versions of my slides…) – watch that here:
